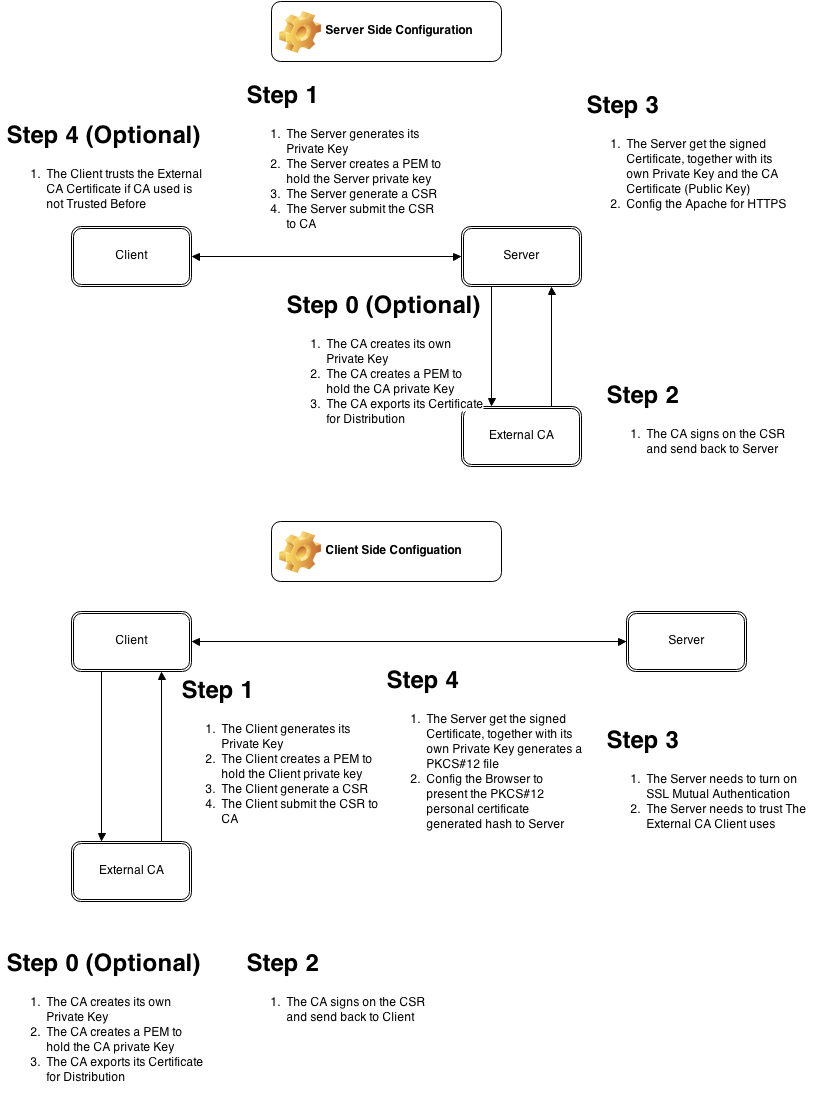
This is Part 2 of the tutorial, after we implement the HTTPS on Server Side, we now configure the server to authentication based on the client key
Please note that the Client CA may not be the same as the Server CA. Client may use its own CA or Veri-sign while Server may use GoDaddy, CheapSSL and etc.
Step 0 (Optional, Skip it if you use external CA like GoDaddy or Veri-sign)
Generate Client CA Private Key
openssl genrsa -out ClientCA.key 2048
Export Client CA PEM
openssl req -x509 -new -nodes -key ClientCA.key -days 1024 -out ClientCA.pem
Export Client CA Certificate
openssl req -new -key ClientCA.key -x509 -days 1095 -out ClientCA.crt
Step 1, On the Client Side
Generate Client Private Key
openssl genrsa -out Client.key 2048
Export Client PEM
openssl req -x509 -new -nodes -key Client.key -days 1024 -out Client.pem
Generate Client CSR to be signed by Client CA
openssl req -new -key Client.key -out ClientForSigning.csr
Step 2, On your CA, Skip it if you use external CA
Use Client CA Key to Sign Client CSR to generate Client Certificate
openssl x509 -req -days 365 -in ClientForSigning.csr -CA ClientCA.crt -CAkey ClientCA.key -CAcreateserial -out ClientCASignedClient.crt
Config Apache to have mandatory SSL Client Authentication
SSLVerifyClient require SSLVerifyDepth 10 SSLCACertificateFile "conf/ssl.crt/ClientCA.crt"
Step 4, On the client side
Package the Client CA Signed Certificate and Client Private Key in PKCS#12 to be imported by Browsers
openssl pkcs12 -export -inkey Client.key -in ClientCASignedClient.crt -out Client.p12
Config the Browser to present Private Key generated Hash to Server while connecting.
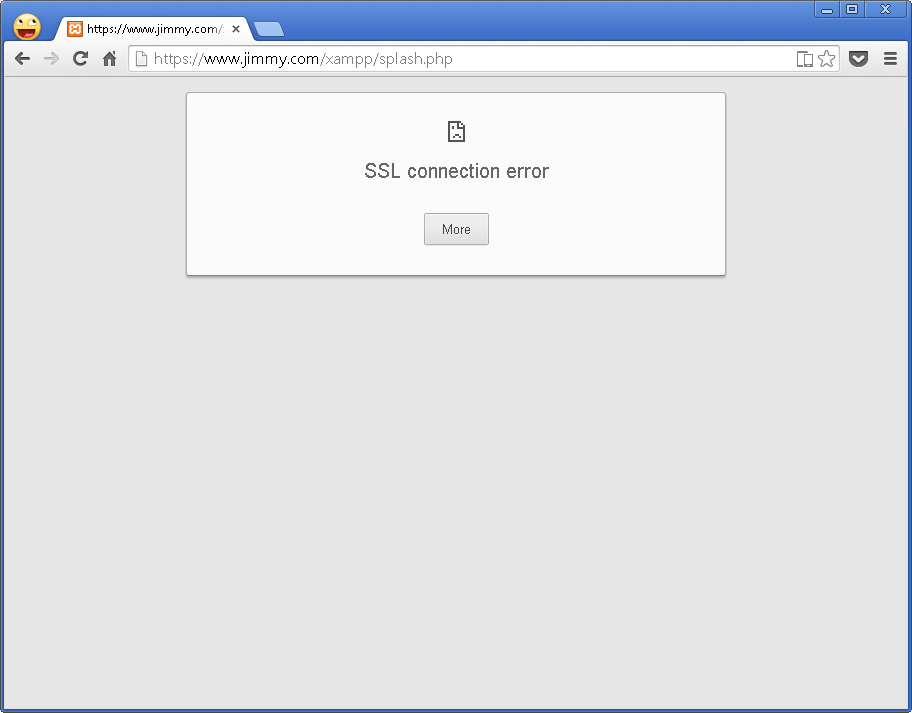
Before Import the PKCS#12 file, Connection should fail
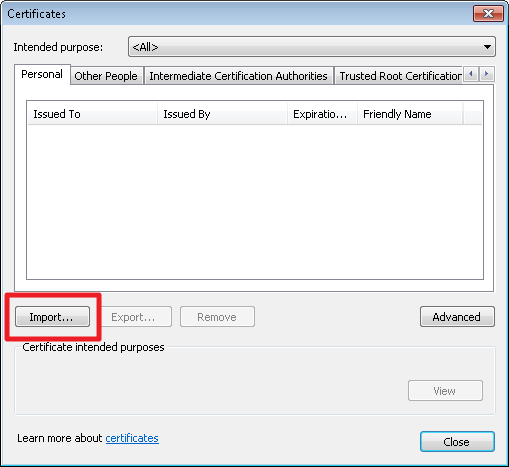
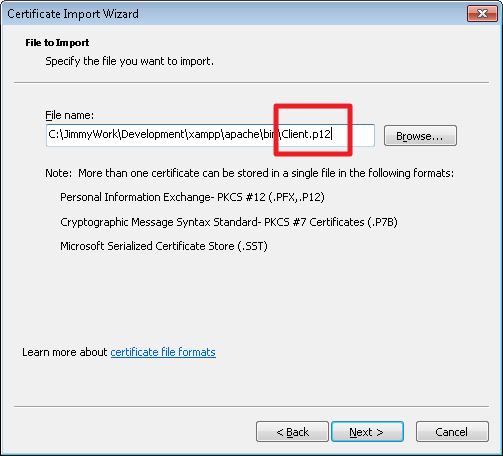
Importing the PKCS#12 file
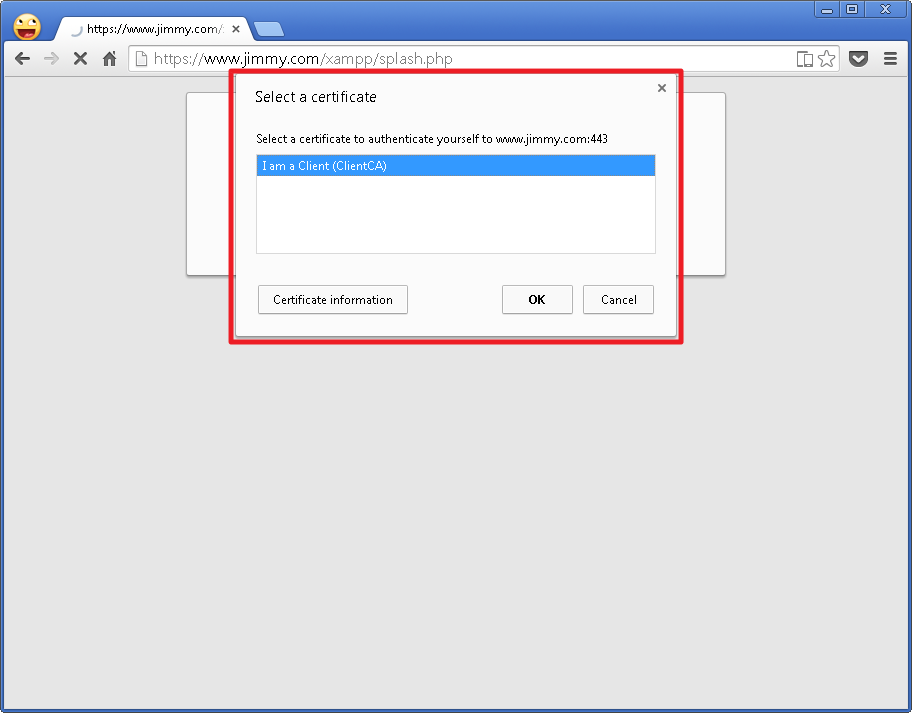
While connecting to Server, select the Identity to be used
DONE!