PGP is a technique that you put encrypted mail content in a standard mail body, like Gmail and Hotmail, by using that technique, you can assure that only the intended recipient can receive and decrypt the mail.
The software we will use is Enigmail and Thunderbird. These two software is available for Mac, Linux and Windows.
PS. For Windows, there are some humor that NSA can decrypt the cipher in Windows, so it MAY not be safe to use PGP in Windows. As I am just a normal user, so no big deal at all.
1. Install Enigmail and Thunderbird (I use Ubuntu, not a big deal for the installation method)
sudo apt-get install enigmail thunderbird
2. Open Thunderbird, add your standard gmail account
If you are using Gmail, you may need to enable the “Less secured logon”, because Gmail has block you from using the classic mail client like Outlook and Thunderbird.
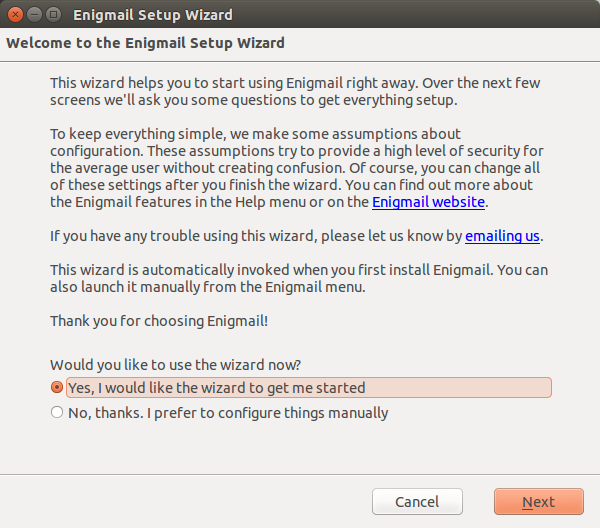
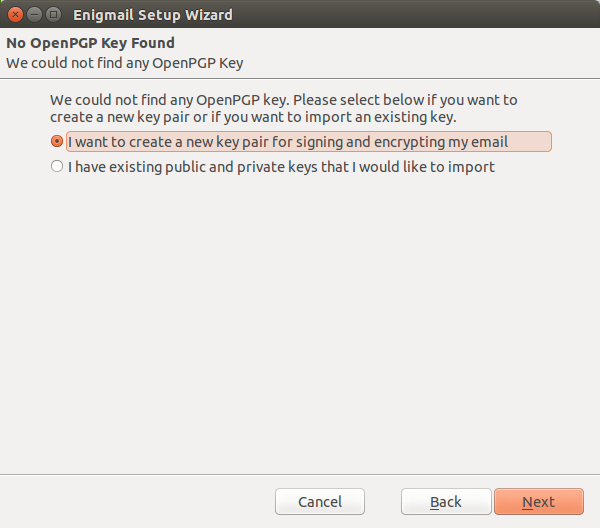
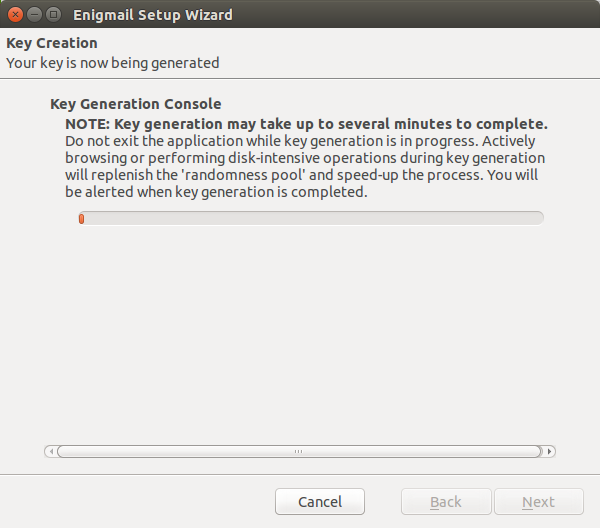
3. Configure Enigmail and Generate the key
You may use Thunderbird, there is a Enigmail menu, Setup Wizard
4. After you generate the key, we can send a PGP encrypted email. I have configured two email with PGP and play around with it.
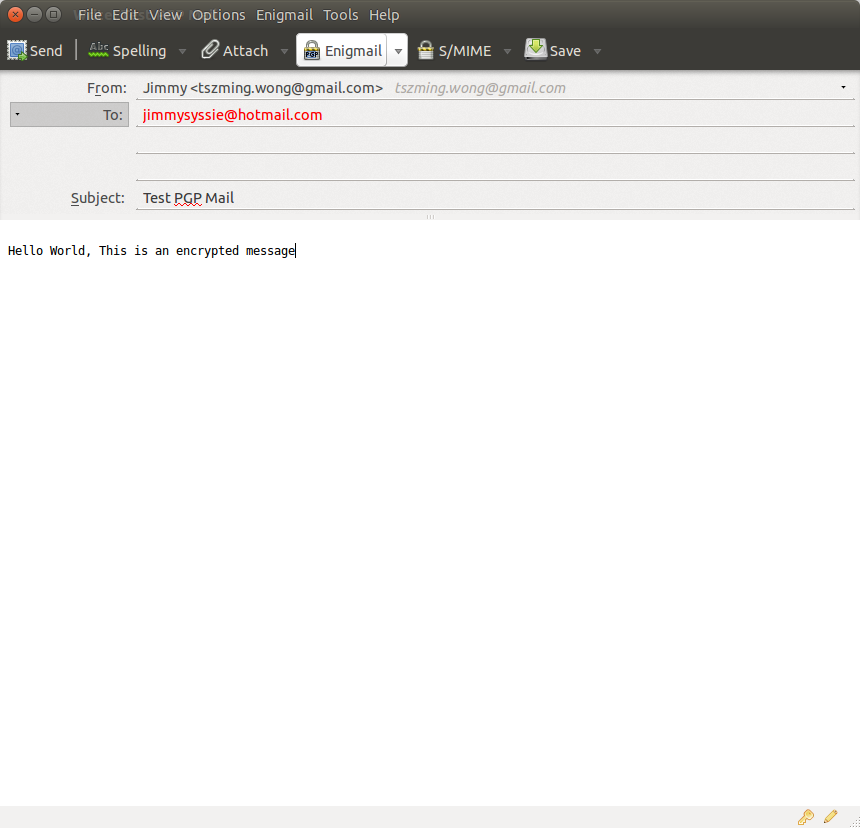
5. After I send out the mail, the mail body is encrypted, but not the Mail Subject (**** IMPORTANT ****). When I click on the sent mail, I don’t even able to retrieve the mail content as it is already encrypted with the recipient public key
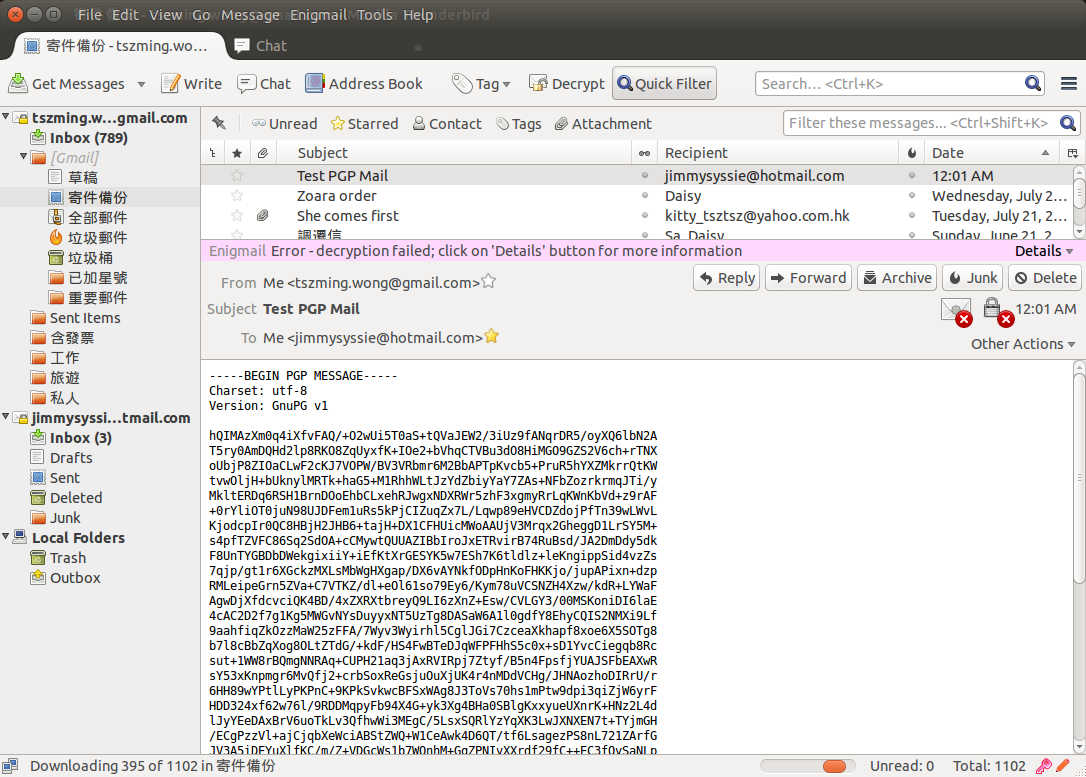
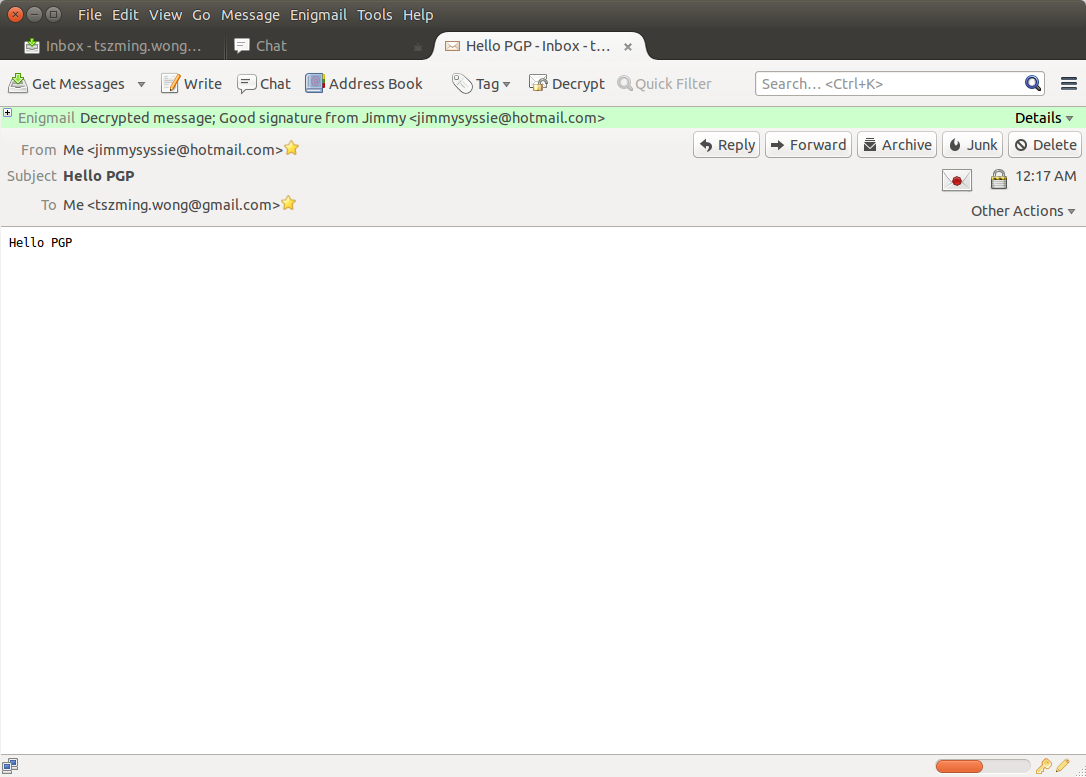
6. On the recipient side, we need to provide password to decrypt the mail body.
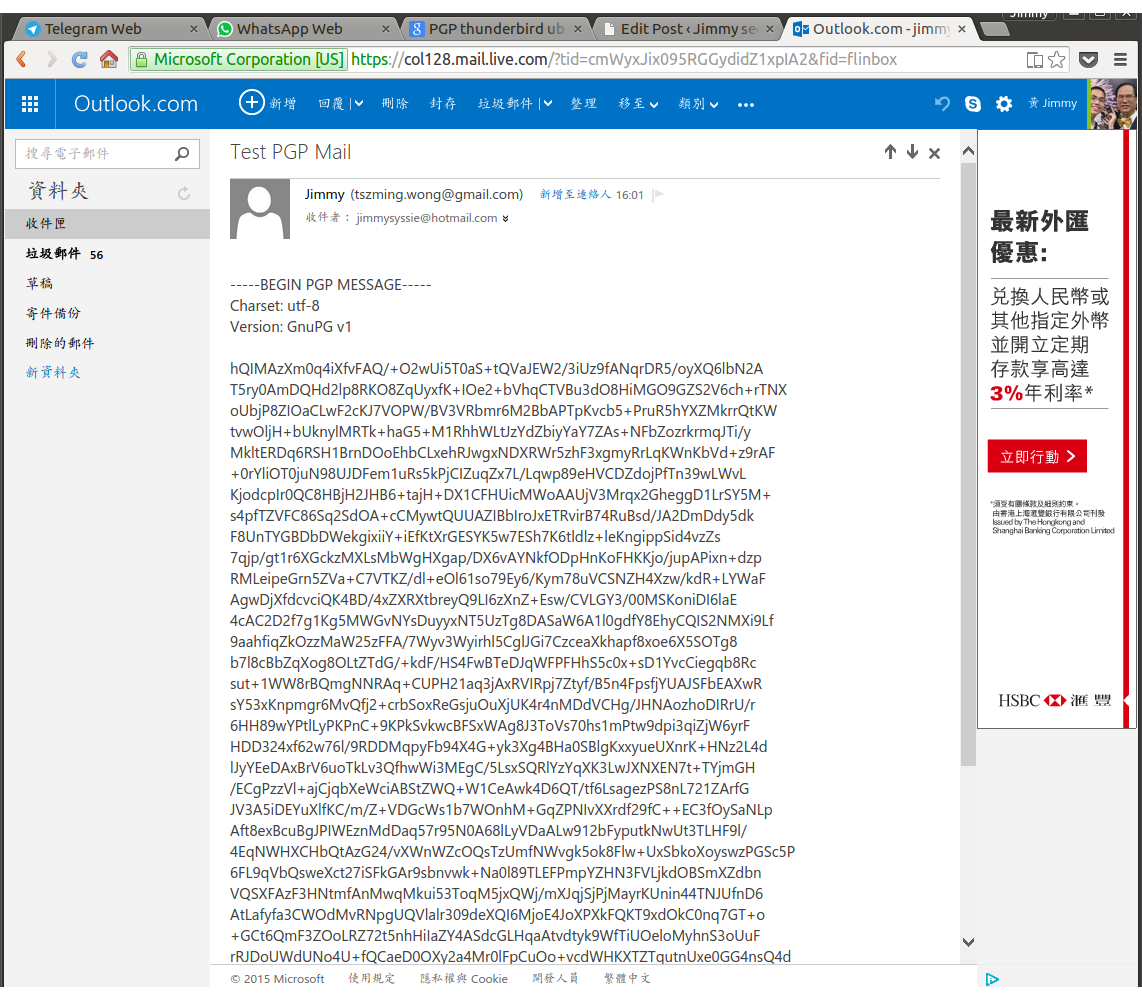
7. If we look at the Web, The content is being encrypted.
8. Finally, you should submit your public key to some public repository, so that other can send u encrypted email.
You may use the export function of Enigmail, publish your public key to key server and every one in the world can send you secured mail.